Work in progress
Overview
IPSec is a framework consisting of protocols and algorithms for protecting data through an un-trusted network such as the internet. IPSec’s protocol objective is to provide security services encrypting sensitive data, authentication, protection and confidentiality.
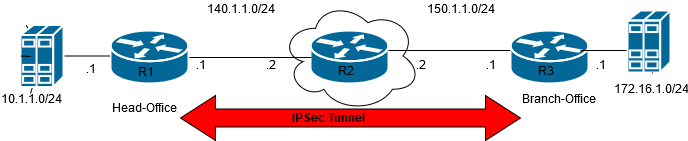
Topology
Instructions
The first step is to configure the interfaces, establish the layer-3 reachability between IPSec tunnel source and destination. Configure the tunnel interface with encapsulation type, specify the tunnel source/remote IP
Configure IPSec parameters for ESP-group and IKE-group with “encryption” and “hash” protocol along with IKE version type to be used
Configure IPSec site-to-site configuration with local and remote peer IP, authentication mode/pre-shared-key, tunnel interface with local/remote prefix for the intended data traffic
Verify the IPSec and IKE tunnel is UP using show commands
Send end-to-end traffic, validate flows are getting encrypted/decrypted at tunnel source/destination end respectively
Configure R1 router (Head-Office)
Configuring IP Addresses, Routing protocol (OSPF) - Enter into exec… mode set interfaces dataplane dp0s3 address 10.1.1.1/24 set interfaces dataplane dp0s4 address 140.1.1.1/24 Tunnel interface used for Source/Destination interface - set interfaces tunnel tun0 local-ip 140.1.1.1 set interfaces tunnel tun0 remote-ip 150.1.1.1 set interfaces tunnel tun0 encapsulation gre set protocols ospf area 0 network 140.1.1.0/24 IPSec VPN configuration - set security vpn ike make-before-break Configure IPSec proposal with esp/encryption/dh/hash alg... - set security vpn ipsec esp-group vm1-esp proposal 1 encryption aes128gcm128 set security vpn ipsec esp-group vm1-esp proposal 1 hash null set security vpn ipsec ike-group vm1-ike ike-version 2 set security vpn ipsec ike-group vm1-ike proposal 1 dh-group 19 set security vpn ipsec ike-group vm1-ike proposal 1 encryption aes128gcm128 set security vpn ipsec ike-group vm1-ike proposal 1 hash sha2_512 Configure IPSec site-to-site parameters set security vpn ipsec site-to-site peer 150.1.1.1 set security vpn ipsec site-to-site peer 150.1.1.1 authenticat mode pre-shared-secret set security vpn ipsec site-to-site peer 150.1.1.1 authenticat pre-shared-secret test123 set security vpn ipsec site-to-site peer 150.1.1.1 default-esp-group vm1-esp set security vpn ipsec site-to-site peer 150.1.1.1 ike-group vm1-ike set security vpn ipsec site-to-site peer 150.1.1.1 local-address 140.1.1.1 set security vpn ipsec site-to-site peer 150.1.1.1 tunnel 0 set security vpn ipsec site-to-site peer 150.1.1.1 tunnel 0 local prefix 10.1.1.0/24 set security vpn ipsec site-to-site peer 150.1.1.1 tunnel 0 remote prefix 172.16.1.0/24
Configure Router-R2
set interfaces dataplane dp0s8 address 140.1.1.2/24 set interfaces dataplane dp0s9 address 150.1.1./24 set protocols ospf area 0 network 140.1.1.0/24 set protocols ospf area 0 network 150.1.1.0/24
Configure R3 router (Branch-Office)
Configuring IP Addresses, Routing protocol (OSPF) set interfaces dataplane dp0s3 address 172.16.1.1/24 set interfaces dataplane dp0s9 address 150.1.1.1/24 Tunnel interface used for Source/Destination interface set interfaces tunnel tun0 local-ip 150.1.1.1 set interfaces tunnel tun0 remote-ip 140.1.1.1 set interfaces tunnel tun0 encapsulation gre set protocols ospf area 0 network 150.1.1.0/24 IPSec VPN configuration - set security vpn ike make-before-break Configure IPSec proposal with esp/encryption/dh/hash alg... set security vpn ipsec esp-group vm3-esp proposal 1 encryption aes128gcm128 set security vpn ipsec esp-group vm3-esp proposal 1 hash null set security vpn ipsec ike-group vm2-ike ike-version 2 set security vpn ipsec ike-group vm2-ike proposal 1 dh-group 19 set security vpn ipsec ike-group vm2-ike proposal 1 encryption aes128gcm128 set security vpn ipsec ike-group vm2-ike proposal 1 hash sha2_512 Configure IPSec site-to-site parameters set security vpn ipsec site-to-site peer 140.1.1.1 set security vpn ipsec site-to-site peer 140.1.1.1 authenticat mode pre-shared-secret set security vpn ipsec site-to-site peer 140.1.1.1 authenticat pre-shared-secret test123 set security vpn ipsec site-to-site peer 140.1.1.1 default-esp-group vm3-esp set security vpn ipsec site-to-site peer 140.1.1.1 ike-group vm2-ike set security vpn ipsec site-to-site peer 140.1.1.1 local-address 150.1.1.1 set security vpn ipsec site-to-site peer 140.1.1.1 tunnel 0 set security vpn ipsec site-to-site peer 140.1.1.1 tunnel 0 remote prefix 10.1.1.0/24 set security vpn ipsec site-to-site peer 140.1.1.1 tunnel 0 local prefix 172.16.1.0/24
Verification
show vpn ipsec sa
vyatta@danos-vnf1:~$ show vpn ipsec sa
Peer ID / IP Local ID / IP
------------ -------------
150.1.1.1 140.1.1.1
Tunnel Id State Bytes Out/In Encrypt Hash DH A-Time L-Time
------ ---------- ----- ------------- ------------ -------- -- ------ ------
0 565 up 2.3K/2.3K aes128gcm128 null n/a 2562 3600
show vpn ipsec status
IPsec Process Running PID: 7020 > Confirm the IPsec process is running
vyatta@danos-vnf1:~$ show vpn ipsec sa
Peer ID / IP Local ID / IP
------------ -------------
150.1.1.1 140.1.1.1
Tunnel Id State Bytes Out/In Encrypt Hash DH A-Time L-Time
------ ---------- ----- ------------- ------------ -------- -- ------ ------
0 563 up 0.0/0.0 aes128gcm128 null n/a 1197 3600
show vpn ipsec state
vyatta@danos-vnf1:~$ show vpn ipsec state
src 140.1.1.1 dst 150.1.1.1
proto esp spi 0xc6708774 reqid 1 mode tunnel
replay-window 0 flag af-unspec
aead rfc4106(gcm(aes)) 0x925793c6057be9a41d9726cd94a3ddb13415e8d0 128
anti-replay context: seq 0x0, oseq 0x0, bitmap 0x00000000
src 150.1.1.1 dst 140.1.1.1
proto esp spi 0xcb9137ef reqid 1 mode tunnel
replay-window 0 flag af-unspec
aead rfc4106(gcm(aes)) 0x4bee7aa173090d179632f0c04c77ddaca7b43927 128
Validation
Finally, to validate IPSec tunnel is able to encrypt/decrypt the packets for configure local/remote prefix - Send ICMP ping packets from Lan1 (10.1.1.0/24) to Lan2 (172.16.1.0/24) network
vyatta@danos-vnf1:~$ ping 172.16.1.1 interface 10.1.1.1 (snipped o/p)
PING 172.16.1.1 (172.16.1.1) from 10.1.1.1 : 56(84) bytes of data.
64 bytes from 172.16.1.1: icmp_seq=1 ttl=64 time=5.46 ms
64 bytes from 172.16.1.1: icmp_seq=2 ttl=64 time=3.38 ms
64 bytes from 172.16.1.1: icmp_seq=3 ttl=64 time=6.26 ms
show vpn ipsec sa
Peer ID / IP Local ID / IP
------------ -------------
140.1.1.1 150.1.1.1
Tunnel Id State Bytes Out/In Encrypt Hash DH A-Time L-Time
------ ---------- ----- ------------- ------------ -------- -- ------ ------
0 633 up 672.0/672.0 aes128gcm128 null n/a 1244 3600
show vpn ipsec sa
Peer ID / IP Local ID / IP
------------ -------------
140.1.1.1 150.1.1.1
Tunnel Id State Bytes Out/In Encrypt Hash DH A-Time L-Time
------ ---------- ----- ------------- ------------ -------- -- ------ ------
0 633 up 1.8K/1.8K aes128gcm128 null n/a 1284 3600
Troubleshooting / Debug commands
show log vpn all
show log vpn ipsec
show vpn debug
Possible completions:
<Enter> Execute the current command
detail Show detailed VPN debugging information
peer Show debugging information for a peer
show vpn debug peer 150.1.1.1
shunt-peer-150.1.1.1-tunnel-0: %any...%any IKEv1
shunt-peer-150.1.1.1-tunnel-0: local: uses public key authentication
shunt-peer-150.1.1.1-tunnel-0: remote: uses public key authentication
shunt-peer-150.1.1.1-tunnel-0: child: 10.1.1.0/24 === 172.16.1.0/24 DROP
peer-150.1.1.1-tunnel-0: 140.1.1.1...150.1.1.1 IKEv2
peer-150.1.1.1-tunnel-0: local: [140.1.1.1] uses pre-shared key authentication
peer-150.1.1.1-tunnel-0: remote: uses pre-shared key authentication
peer-150.1.1.1-tunnel-0: child: 10.1.1.0/24 === 172.16.1.0/24 TUNNEL
shunt-peer-150.1.1.1-tunnel-0: 10.1.1.0/24 === 172.16.1.0/24 DROP
peer-150.1.1.1-tunnel-0[24]: ESTABLISHED 3 hours ago, 140.1.1.1[500][140.1.1.1]...150.1.1.1[500][150.1.1.1]
peer-150.1.1.1-tunnel-0[24]: IKEv2 SPIs: a9122ec476067169_i 6e154e0afe6d0a04_r*, pre-shared key reauthentication in 4 hours
peer-150.1.1.1-tunnel-0[24]: IKE proposal: AES_GCM_16_128/PRF_HMAC_SHA2_512/MODP_1536
peer-150.1.1.1-tunnel-0{189}: INSTALLED, TUNNEL, reqid 14, ESP SPIs: cbc4b9e9_i c3360c54_o
peer-150.1.1.1-tunnel-0{189}: AES_GCM_16_128/MODP_1536, 0 bytes_i, 0 bytes_o, rekeying in 34 minutes
peer-150.1.1.1-tunnel-0{189}: 10.1.1.0/24 === 172.16.1.0/24
How to check it is working or ideas on how to troubleshoot.